Enigmedia visits Schneider Electric’s OT Laboratory
Enigmedia (Certified Technology Partner of Schneider Electric) has recently been invited by Schneider Electric to its laboratory at the Andover Competence Center, Boston, to hold a technical session for members of their Process Automation and Industrial Cybersecurity team.
The main objective of the session is to carry out a demonstration of Enigmedia’s MUGA product to understand in detail the operation and differential value of this solution in an industrial production environment emulated in said laboratory.
During the session, Enigmedia team explained the functionalities of the solution and the deployment and configuration process. Once going through an in-depth understanding of the solution, the real demonstration of the technology is carried out in the test environment, aiming to protect the devices of the industrial control system against certain common cyberattacks which tend to occur in this type of environment.

Initial scenario: a flat industrial network
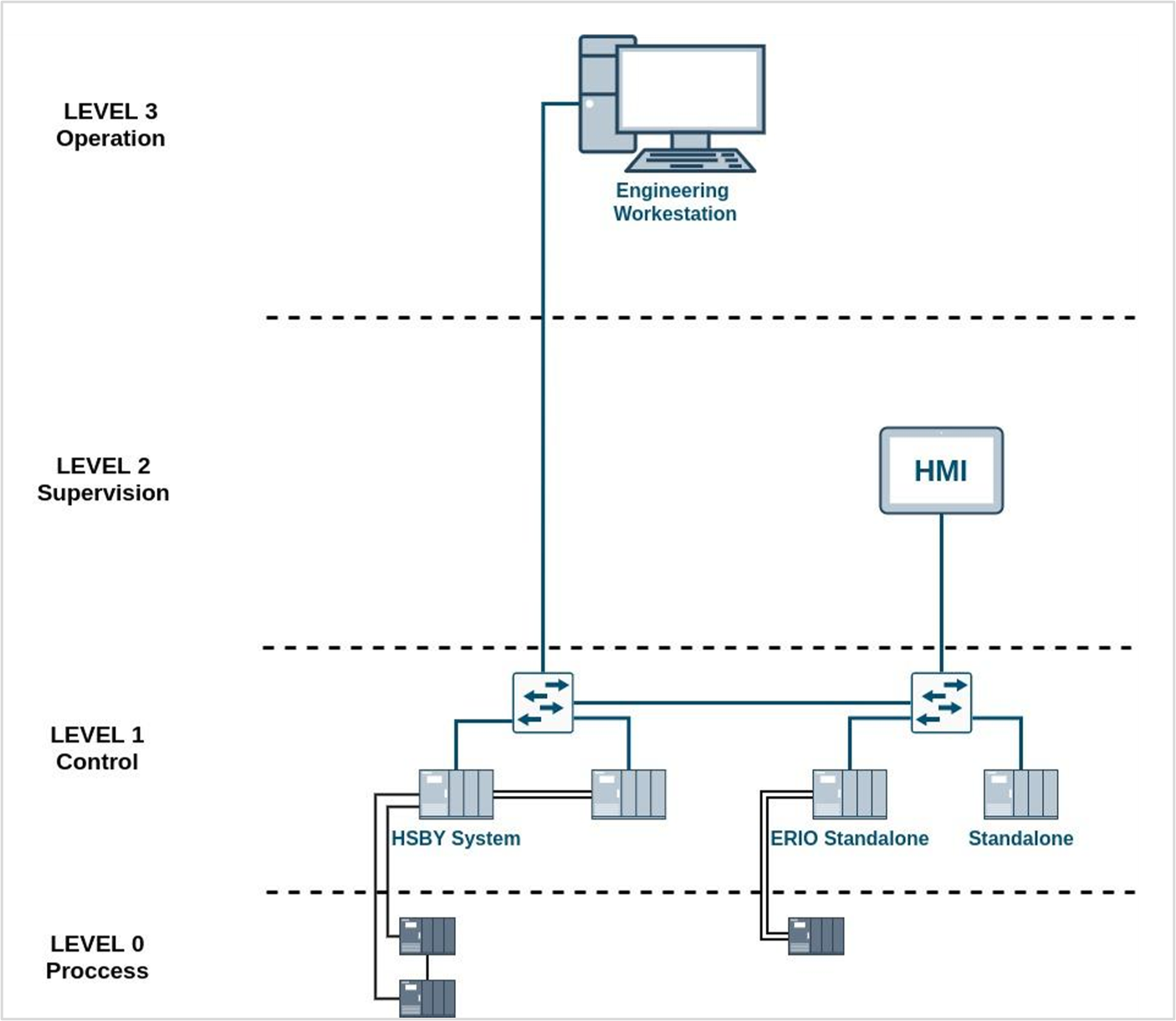
The proposed test environment consists of a flat network that emulates an automated production process in an industrial plant. The network includes multiple Schneider Electric OT elements such as PLCs, an HMI, switches, an EWS and some actuators, replicating, on a small scale, a standard industrial control system.
Today, it is very common to find flat networks with few security measures implemented, both in industrial plants and in critical infrastructures. In this scenario, Enigmedia’s technology shine bright, as it is has been designed to protect flat brownfield networks with the minimum impact in the current architecture. This implies that no reconfigurations are needed as a L2 overlay is created once the solution is deployed, avoiding changing devices, IPs and other complex reengineering processes.
The diagram below shows the architecture proposed by Schneider as the initial scenario.
Main risks of a flat industrial network
Flat networks are the most vulnerable network we can find, and unfortunately the most common in legacy industrial environments, as they were designed to be isolated and not connected. Most industrial enterprises are just getting started with their OT cybersecurity strategy, meaning that they are still taking the first steps in their industrial cybersecurity roadmap. Usually within these first steps asset inventories and network auits are done in order to plan further measures based on network topologies. However, most companies lack from advanced steps such as network segmentation, secure conduits between zones, user authentication or communications encryption.
When a threat or attacker gains access to flat networks, the main risks are:
- All the network devices are visible to an attacker, so they can exploit existing and known vulnerabilities.
- A single infected device or system can affect the entire network, as all items are accessible from within the network.
- An attacker can perform lateral movements in case of penetration.
- There is no segregation of communications, so all devices can communicate with each other.
- Flat networks are the ideal environment for an “insider” (a malicious actor with legitimate access to the network, for example, an employee), since they can access systems that are outside their authorized scope of action.
Today it is urgent to apply cybersecurity measures to industrial flat networks, although it is not easy since there are specific challenges related to networks, devices, and production processes, that make it difficult and costly.
Main challenges found when protecting the proposed OT network
In the initial scenario, we found some difficulties that are very common when protecting brownfield industrial networks which are already deployed and in operation. These challenges are related to reconfiguration requirements that imply complex processes and usually must be executed locally by an expert. These reconfiguration processes may cause production downtime and/or system malfunction.
The issues detected by the technical teams of Schneider and Enigmedia were the following:
-
- Impossibility to configure PLCs remotely. To configure the PLCs, it is necessary to connect a PC running the PLC configuration software via USB (serial port), and then install the new configuration to the PLC. This requires an expert technician in the field, and long-time execution for one-by-one reconfiguration
- Downtime when changing the PLC’s IP. When making IP changes, the PLCs do not always reconnect correctly. They may take a long time to be operational again. When changing IP, communication between parts of the system is lost, and synchronization processes must be initiated between the elements of the system. This requires specialized personnel in the field and considerable time to recover the process.
- Dependencies between devices. Some PLCs are interdependent, so a specific updating hierarchy must be followed. If an error occurs in this sequence, it will imply restarting the devices manually (switch off / on) or connect via USB to load the new configuration directly from a PC. This again implies risks of unwanted and long downtimes.
- Human error: if an error occurs when reconfiguring an IP (human error) the system stops working correctly and it is necessary to turn on and off several computers until the system is revamped. In large systems this error is likely to occur and involves longer downtime.
How to protect OT network with MUGA
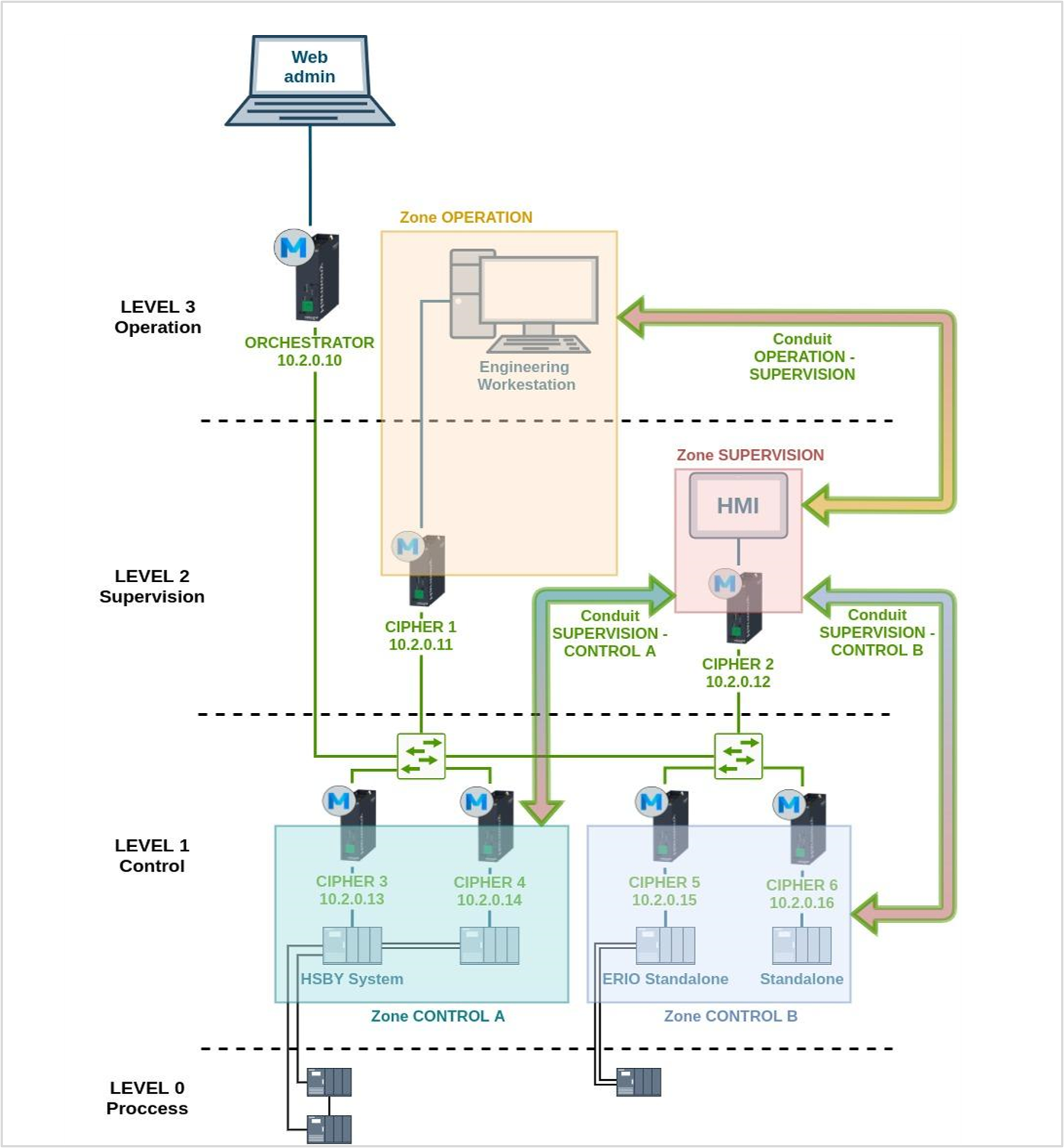
Starting from the flat network described previously, the session consists of deploying MUGA in an easy and fast way, demonstrating that existing devices can be protected avoiding reconfigurations. Then, after deployment, show how security functionalities (such as encryption, segmentation, and firewall) can be easily implemented.
By deploying Enigmedia’s MUGA solution, an advanced security layer is created on top of the OT network hiding assets and allowing micro-segmentation, conduits definition, firewall rules, and encrypted communications between the different zones. All this is achieved with minimal impact on the architecture and network performance and avoiding reconfigurations and devices replacement.
MUGA consists of two key elements:
- MUGA Nodes: appliances that run MUGA software within Schneider IoT Box hardware which are deployed in the field at PLC level or to selected switches depending on the network topology and requirements. MUGA Nodes act as ciphers and create secure zones by authentication and encryption (crypto-segmentation).
- MUGA Orchestrator: it is is deployed in the DMZ (or higher levels) and includes a simple and intuitive control panel to configure and manage the MUGA Nodes.
The following diagram shows how to protect the proposed network with MUGA.
Protection with Enigmedia against common OT attacks
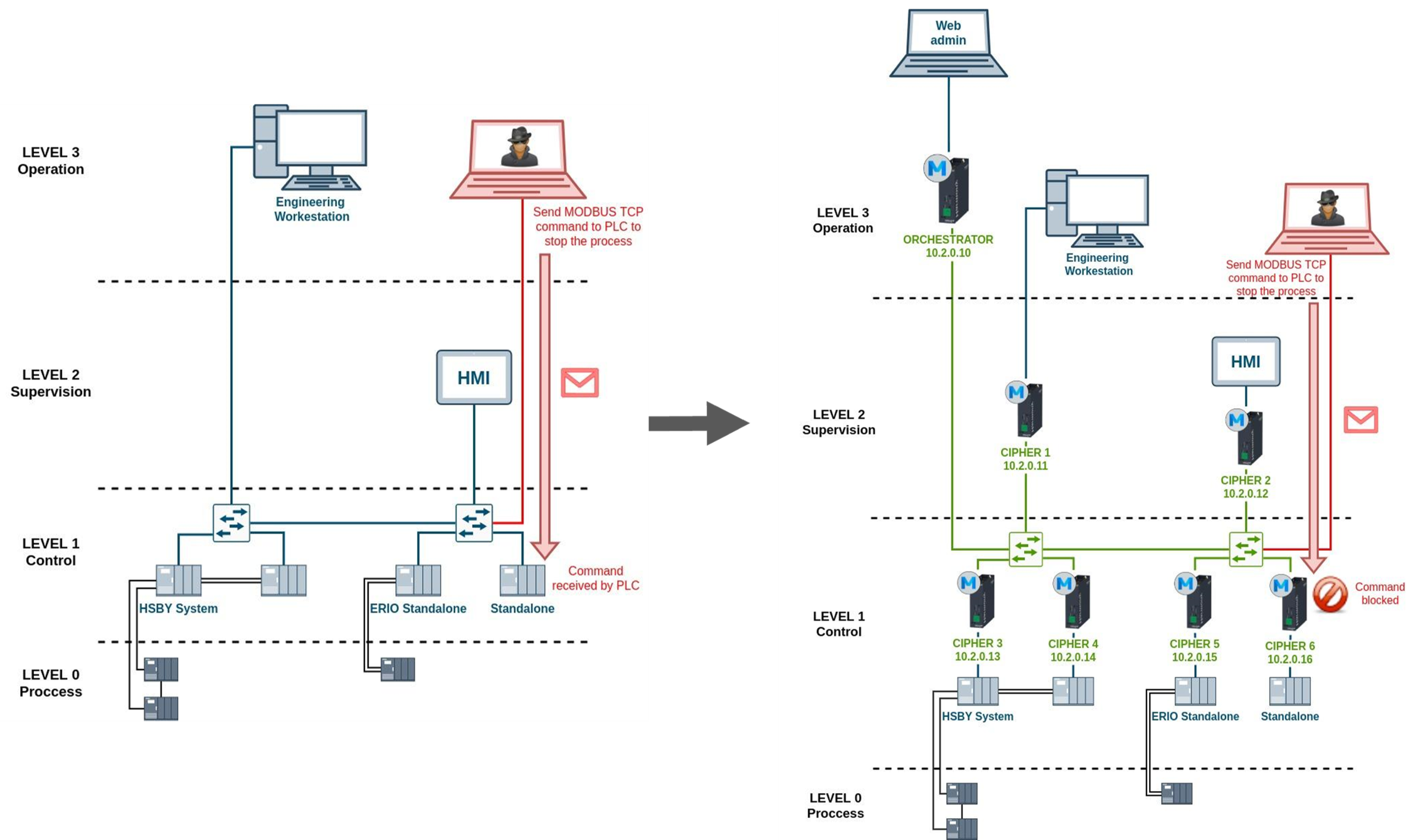
Throughout the demo, the following tests are performed to test the value MUGA brings to protecting OT networks. During these tests, it is verified that the solution encrypts the network traffic without any impact on latency, and then simulates some attacks directed at the PLCs to stop the production process and how the implanted solution can prevent them.
First, a PC is connected to the SPAN port of the switch to simulate that an attacker has gained access to the network. Without the implemented solution, and using Wireshark, it is proven that the traffic is clear, and that the attacker may filter MODBUS traffic and see the IPs of the PLCs. After this, MUGA is displayed and it is verified that the traffic is encrypted and MODBUS is not seen, thereby preventing an attacker from obtaining information from the network.
Once it has been verified that the traffic is encrypted when implementing the solution, we proceed to demonstrate how MUGA prevents attacks:
- First (without implementing MUGA) an attack is launched with a malicious attachment to check if the system is still working. Malicious attachment causes PLCs to shut down, completely stopping the production process.
- Once MUGA is implemented, the attack is launched again, and it is verified that it does not affect the network since the attack cannot reach the PLCs thanks to the secure layer of protection that is created when the MUGA Node is deployed.
Below are some of the testimonials made by members of the Schneider Electric team who attended the session, including specialists in process automation and cybersecurity.
“Great product demonstration. Super fast installation and configuration. Great for brownfield plants”
“This was a great demonstration as to how easily and with minimum downtime you can help protect the system”
Please get in touch if you want to know more about how Enigmedia helps solving OT cybersecurity challenges:
https://enigmedia.es/company/contact/
Enigmedia is a Cerified Technology Partner of Schneider Electric. You can also find our solution in SE Exchange marketplace:
https://shop.exchange.se.com/en-US/apps/44917/mercury-cipher
Related posts:
- OT Cybersecurity Roadmap based on IEC-62443: https://enigmedia.es/2021/07/26/ot-cybersecurity-roadmap-based-on-iec-62443/
- Mitigating Cyber Risks in the age of OT/IT Convergence: https://enigmedia.es/2021/07/02/mitigating-cyber-risks-in-the-age-of-ot-it-convergence/
- Introduction to the great unknown world of OT Cybersecurity: https://enigmedia.es/2021/06/24/introduction-to-the-great-unknown-world-of-ot-cybersecurity/