Crypto-segmentation: a new approach for OT network segmentation
A very common case that we are seeing constantly week after week is the rapidly increasing amount of threats and vulnerabilities in the control systems within critical infrastructures and industrial environments. This is mainly due to the strong dependence on legacy systems in which updating, patching and making corrections without impacting on the availability and integrity of operations is not an easy task, or even being impossible in many cases.
Moreover, it is very usual to find completely flat OT networks in these environments with security measures barely implemented as these networks tended to be completely air-gapped from IT and corporate systems. This implies that any malicious actor trying to penetrate the network will easily get through and move laterally with complete freedom, identifying critical assets or communications and therefore discovering vulnerabilities and exploiting them.
It is now traditional in IT networks to implement proactive security measures such as network segmentation, and it is common sense to do so in any network where applications, devices, data and communications live together. The roots of network segmentation run deep in enterprise IT environments, but are not so common in OT networks. Recently developed industrial security norms such as IEC-62443 are now recommending to implement a network segmentation as one of the first steps for a successful industrial security strategy. However, it is not as easy as it seems in many cases due to the complexity of these networks.
Traditional approach to OT network segmentation
Unlike in IT environments, a cyberattack can target water facilities, power plants, pipelines, railway systems, or hospitals, defense is about critical infrastructures, industrial processes, critical assets, the environment, and, most importantly, human safety.
Traditionally, perimeter security measures were implemented to protect these environments, but they have resulted to be insufficient over time. To overcome this, organizations started to establish the proper zones with clearly defined and enforced security policies, better known as network segmentation. This segmentation is highly related with the physical architecture of the networks, but in many cases, it is not related to the real business operations where different external agents intervene such as operators, maintenance, vendors and so on.
Additionally, traditional segmentation using NAC solutions such as VLAN, VPN or DMZ present many difficulties when trying to deploy them, due to the heterogeneity of OT networks, device management, legacy protocols and IP configurations. It can even have an impact on the performance of these networks where latencies are critical for operational continuity. The traditional approach to network segmentation can also add complexity to authorized access management, which is a serious problem nowadays with the rise of remote access in OT networks.
Crypto-segmentation as a new approach
In order to address the problems that traditional segmentation brings to OT networks and to strengthen their security, a new approach can be implemented called Crypto-segmentation. This approach takes network segmentation to the next level by adding strong cryptography to enforce network logic. It is designed for complex networks which require being more accessible from other networks and external agents such as maintenance or suppliers, and where trust based measures are not enough to ensure strong security. Crypto-segmentation is the perfect way for a transition from traditional perimeter security to “Zero-Trust” approach.
This approach is based on the creation of crypto-segments (groups of devices and applications) independent of the physical and logical network, being able to encompass devices which are in different physical or logical networks. These zones have their own cryptographic keys to secure and segregate traffic end to end as it travels across the network. Crypto-segmentation is deployed as an additional overlay, cloaking assets without the need to change configurations or replace devices and therefore avoiding friction with operations and minimizing downtimes.
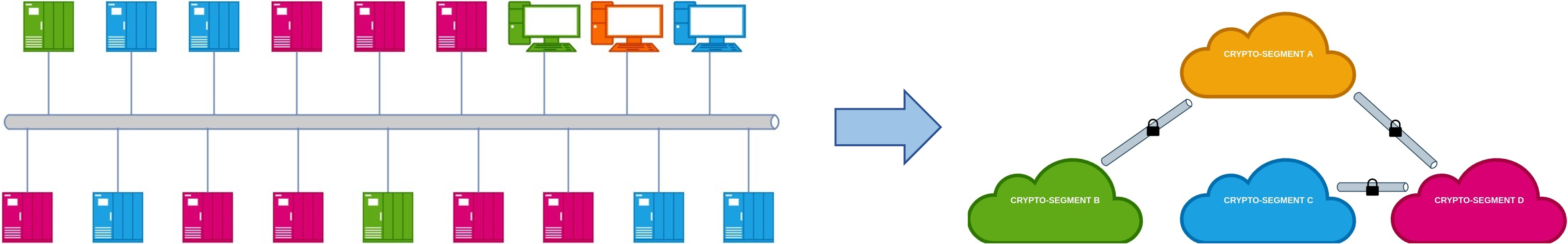
The following benefits of crypto-segmentation are outlined compared to the traditional network segmentation:
- It is more secure as it adds strong encryption and access controls based on user roles
- More flexibility as it is independent of configurations, traffic and the technologies used, being easily adapted to OT network challenges
- Easier to manage, as an overlay is created and can be configured and managed as a SDN, implying no modification of the current infrastructure
- Centralizes and simplifies security policy management
- Independent from the existing network
- Assures availability, integrity and confidentiality of industrial communications
- Minimizes the attack surface and visibility of legacy non-patcheable devices
- Increments the security of industrial protocols as it adds authentication and encryption
- Security policies are based on business logic and not only in the network architecture
- Eliminates lateral movements of attackers
Crypto-segmentation is an advanced security measure, solving the usual challenges that arise when increasing the security level of OT networks and trying to be compliant with the highest security standards such as IEC-62443.
If interested in applying a crypto-segmentation approach to OT networks, do not hesitate to get in touch with us and we will be happy to explain in more detail how our solutions can help you to deliver crypto-segmentation in the best possible way.
Author: Joaquín Santodomingo – Product Manager at Enigmedia
Related links:
Enigmedia contact page: https://enigmedia.es/company/contact/
MUGA for OT network protection following IEC-62443 with crypto-segmentation: https://enigmedia.es/products/muga/
Enigmedia is a Certified Technology Partner of Schneider Electric. You can also find our solution in SE Exchange marketplace: https://shop.exchange.se.com/en-US/apps/44917/mercury-cipher
