The use of Zero Trust security in OT networks
Critical infrastructure and industrial companies are crucial in our day to day lives as they provide clean water, electricity, vehicles or consumer goods amongst many other basic needs we may have. However, we are mostly unaware about the complexity of the operations, systems and technologies being used to keep them running.
In the past decades, with the advent of technology automation of critical operations and industrial processes has been implemented in order to achieve optimum efficiency, safety and cost-effectiveness. The technology that has helped along the way and made this possible can be categorized as Operational Technology (OT), encompassing the computing systems that manage industrial operations, better known as Industrial Control Systems (ICS) which include Supervisory Control and Data Acquisition (SCADA), Distributed Control Systems (DCS) and other subsystems.
OT enables plant operators to control and monitor sensors, actuators and other electro-mechanical processes, for example, opening and closing valves or controlling water temperature. Also, valuable data from operations such as manufacturing processes across globally distributed plants can be collected and linked in real time to enterprise applications such as ERP for optimum performance.
Nevertheless, this operational efficiency also brings with it many risks and threats linked to the hyperconnectivity and rapid digital transformation in the industrial environment. The exposure of these systems has increased dramatically, opening the door to cyber-criminals and targeted attacks which can have a huge negative impact on society, the economy or the environment if they stop working.
Can Zero Trust be extended to OT?
In order to overcome the threats related to industrial digitisation and to improve the insufficient traditional security methods such as perimeter defense, new security paradigms and frameworks have emerged such as Zero-Trust. This concept is mainly based on the belief that organizations must verify anything and everything trying to connect or access its systems without trusting anything inside or outside its perimeter.
In traditional IT systems, Zero-Trust has been a top trend and works great in this kind of environment as many systems and applications can work independently. Adding to this, humans login to IT systems with authentication mechanisms such as username, password, 2FA and more. On the contrary, OT systems mostly interact with machines working autonomously and they tend to lack authentication as it was not needed in the past. Therefore, implementing a Zero-Trust model to OT is still being questioned as it may cause disruptions to the operations and systems, due to the fact that many brownfield systems coexist within industrial plants and critical infrastructure. Additionally, most industrial systems have been designed to have very long amortization periods, therefore OT systems such as ICS tend to have a high volume of legacy devices, unpatched operating systems and many critical vulnerabilities.
Devices such as PLC, controllers and other Purdue Level 1 and the most vulnerable as they have been built with no security in mind, lacking basic authentication and data protection mechanisms. Basically, there are no security controls when accessing these devices or sending control and administrative commands so it is hard to think of a real Zero-Trust approach within OT systems. Hence, until total trust is removed from ICS and basic security features such as authentication and encryption are added, we will not be able to get the most out of Zero-Trust in industrial environments.
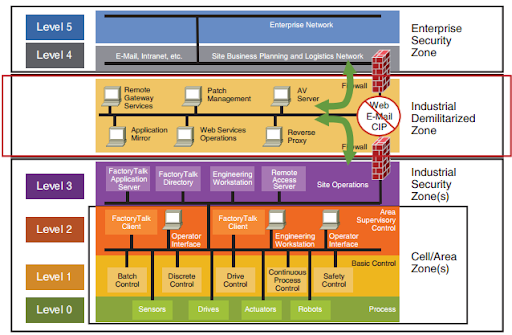
How to start implementing Zero Trust security in OT
To properly implement advanced security models in OT, we must adapt them for these specific environments and make sure they are dynamic, as OT is very heterogeneous and security mechanisms are evolving continuously. Having an efficient Zero-Trust in real-time operations is a difficult challenge, specially in lower layers such as PLC or DCS plant based systems. However, there are security measures that can be applied in order to get data securely across the network and avoid natural trust within devices and applications.
As mentioned above, one of the main challenges is the vast amount of legacy devices coexisting in these systems. Thus, authenticated devices and encrypted communications are something impossible in most cases unless they are replaced with greenfield systems. This may be a very costly task as it leads to operational downtimes and production loss, plus expensive infrastructure investments. With this said, implementing measures based on Software-Defined Networking (SDN) can be compensatory for approaching a Zero-Trust model in OT systems. A secure overlay can be delivered through SDN, obfuscating critical assets without the need to replace devices and avoiding complex network reengineering. In addition, strong authentication can be added for communications within the SDN and for accessing devices underneath the overlay.
Similar but not identical to SDN, crypto-segmentation can also be a countervailing measure and can mitigate the risks related to traditional segmentation based on NAC such as VLANs. With crypto-segmentation, multiple zones can be defined based on critical assets, production processes or customized segmentation requirements. Also, trust within the network is eliminated as this mechanism uses strong cryptography to enforce segmentation logic, including zones with its own cryptographic keys to secure and segregate traffic as it travels across OT networks from end to end. This completely separates segmentation from underlying infrastructure and technology, being fully compatible with legacy devices and industrial protocols. If you want to learn more about crypto-segmentation in OT, check our previous blog article here:
https://enigmedia.es/2021/09/30/crypto-segmentation-approach-for-ot-network-security/
Extracting data from OT systems for monitoring and analytics following a Zero-Trust approach can also be challenging. Modern devices can send data directly to control and monitoring applications, however, this is mostly done with no security in mind. In other cases, data can be extracted from OT networks by sending traffic through a SPAN port directly to the applications stack, but again, without any encryption and lacking authentication. Therefore, using sensors with advanced security features such as PKI based authentication and lightweight encryption can take you a step closer to Zero-Trust and will ensure data protection for industry 4.0 initiatives.
These are some, but not all, of the measures to take in order to achieve Zero-Trust in your OT networks without having to replace the entire infrastructure with state-of-the-art systems. By adding encryption and authentication to the lower layers through the implementation of OT cybersecurity technologies such as SDN, together with secure data collection and sending, you can protect devices, processes and communications across entire OT networks, eliminating deeply flawed trusted networks which are highly ineffective at stopping today’s cyberattacks.
For more information on how to implement a Zero Trust security model into OT networks please contact us:
Enigmedia is a Cerified Technology Partner of Schneider Electric. You can also find our solution in SE Exchange marketplace: https://shop.exchange.se.com/en-US/apps/44917/mercury-cipher
